Sunday, December 14, 2014
TEN MYTHS ABOUT PASSWORDS IN WINDOWS
101 COMBINATION ON THE KEYBOARD, WHICH CAN MAKE YOUR LIFE EASIER

If you work a lot with the computer, then you know that for a quick and productive work should try to do without the mouse. In this edition of Science and Technology will explain how it is more convenient to use: Windows, Chrome, Firefox, Gmail, Mac, MS Excel, MS Word, Google
Ctrl + L or ALT + D or F6 - go into the address bar and select its contents;
Ctrl + K or Ctrl + E - go to the address bar and enter a query to the selected default search engine;
Ctrl + Enter - turn tratata in the address bar in www.tratata. com :)
Ctrl + T - new tab;
Ctrl + N - a new window;
Ctrl + Shift + T - return the last closed tab;
Ctrl + Shift + N - secret level "Chrome" :) New Window in "Incognito";
Shift + Esc - one more secret level :) Built-in Task Manager;
Ctrl + Tab or Ctrl + PageDown- as elsewhere, leaf through the tabs from left to right;
Ctrl + Shift + Tab or Ctrl + PageUp - leaf through the tab from right to left;
Ctrl + 1, ..., Ctrl + 8 - switches between the first eight tabs;
Ctrl + 9 - switches to the last tab;
Backspace or Alt + Left Arrow - go to the previous page in the history of the current tab;
Shift + Backspace or Alt + Right Arrow - go to the next page in the history of the current tab;
Shift + Alt + T - switch to the keypad instruments; thereafter it is possible to move left and right arrows, and select the button by pressing Enter;
Ctrl + J - open tab all downloads;
Ctrl + Shift + J - open the Developer Tools (View menu item code);
Ctrl + W or Ctrl + F4 - Close the active tab or pop-up window;
Ctrl + R or F5 - as elsewhere, update (tab open);
Ctrl + H - Open tab history (History);
Ctrl + Shift + Delete - window cleaning history;
Ctrl + F or Ctrl + G - search for text on the open page;
Ctrl + U - view the HTML-source code of the page; By the way, the address bar type of view-source: POLNYY_URL show from this source URL;
Ctrl + O - as elsewhere, a file open ... and the "File" menu does not need to look for;
Ctrl + S - similarly - to save the current page;
Ctrl + P - print the current page;
Ctrl + D - Bookmark, like most browsers;
Ctrl + Shift + B - open the Bookmark manager;
Alt + Home - to return to the home page;
Ctrl ++ (plus), Ctrl + - (minus) - Zoom in and zoom out; "Plus" and "minus" can be normal or gray;
Ctrl + 0 - return to the display scale of 100%;
F11 - full screen and back.
Open links in a "lame" is also useful if you get used to, and the right mouse button is not needed:
Ctrl + click on the link (option - click on the link to the middle mouse button or scroll wheel) - open the link in a new tab on it;
Ctrl + Shift + click on the link (Option - Shift + click on the link to the middle mouse button or scroll wheel) - open the link in a new tab switching to it;
Shift + click a link - Open link in a new window.
Firefox
- Raise or lower the page. Spacebar - Drop Down Arrow, Shift + Spacebar - lift page.
- Find. Ctrl + F or Alt-N to the next page.
- Add this page to your bookmarks. Ctrl + D.
- Quick Search. /.
- New tab. Ctrl + T.
- Go to the search bar. Ctrl + K.
- Go to the address bar. Ctrl + L.
- Increase the size of the text. Ctrl + =. Reduce the size of tekstaCtrl + -
- Close the tab. Ctrl-W.
- Reload the page. F5.
- Go to the homepage. Alt-Home.
- Restore the page is closed. Ctrl + Shift + T.
- Bookmarks with keywords. This is the most productive. If you frequently visit a website, you are doing a bookmark (of course!), Then go to the properties tab (click on it, right-click). Add a short keyword in the keyword input, save, and then you can simply enter in the address bar (Ctrl + L) is the key word, and immediately proceed to the site.
Gmail
- Write a new message. C.
- Reply to the letter. R.
- Respond vsem.A.
- Send a letter. F.
- Save the current message and open the next pismo.Y + O.
- Delete the message and open the next. # + O (or Shift-3 + O).
- Send a written letter. Tab-Enter.
- Search. /.
- Navigation. Moving down J and vverhK list of contacts.
- List of messages. N and P move the cursor to the next or previous message, and the message list.
- Ignore. M- letters with distinguished addresses are no longer exposed to the list of incoming messages and archived.
- Select conversation. X - The conversation will be selected. It can archive, apply a label to it and choose for her action.
- Save Draft. Control-S.
- Go to the message list. G + I.
- Go to the marked letters. G + S.
- Go to the address book. G + C.
Windows
- Create shortcuts to quickly switch. To create a keyboard shortcut to quickly switch, right-click on the icon create shortcut switch (there is one on your desktop) and enter the combination. For example, such as Ctrl-Alt-W to of Word.
- Switch between windows. Alt-Tab - select the window you want, then lower the key. Or hold down the Windows, click on Tab to go through the taskbar button and find the right window, and then, having found it, then press Enter.If you add the Shift key to any of these methods, the selection window will be in the opposite direction.
- Go to the desktop. Key Windows-D.
- Context menu. Instead of right click, press Shift-F10. Then scroll up or down using the arrow keys up and down.
- Shut down. To quickly turn off the computer, press the Window, and then U. With this button you can press on S to pause, to turn on the U or R to reload.
- The most common. You, of course, you know, but for beginners should mention the most famous combination: Ctrl-O- open, Ctrl-S - save, Ctrl-N - open a new document, Ctrl-W - close the window, Ctrl-C -kopirovat, Ctrl -V - paste, Ctrl-X - cut. Ctrl-Z - undo (back), Ctrl-Y - cancel (forward). To see the contents of the clipboard into MS Office, press Ctrl-C twice. Ctrl-Home- go to the top of the document, Ctrl-End - go to the end.
- Menu. When you press Alt, a menu appears in which you want to work, using the arrow keys. Alt plus the underlined letter of each menu option leads to the use of this option. Or simply remember the keyboard shortcut for this option for even more rapid use.
- Explore Windows (Explorer). Windows-E - program runs My Computer.
Operating system Mac
- Switch Dock. Option-Cmd-D - show / hide the Dock.
- Hide all the rest. Cmd-Option-H hides all other windows except the one in which you are located. Facilitates your screen.
- Close the window. Cmd-W closes the active window open. Option-Cmd-W closes all open windows.
- Open directory. Option-Cmd-right arrow - deploy directory and subdirectories in the list in the Finder.
- Forward and backward. Cmd- [andCmd-] worked with the Finder, Safari and Firefox.
- Copy screen. Cmd-Shift-3 - for the entire screen. Cmd-Shift-4 - creates a border to copy the selected part of the screen.
- Exit. Shift-Cmd-Q - output realized after 2 minutes. Shift-Option-Cmd-Q - output realized immediately.
- Empty Recycle Bin. Shift-Cmd-Delete.
- New window in Safari. Cmd-T.
- Help. Cmd-shift- ?.
- Load CD. Press C during startup (just after the melody), download CD.
- Boot from another department. Option-Cmd-Shift-Delete- starts to boot, until you find another department, such as a CD or disk.
- Additional Information. Cmd-Option-I open a window with additional information that allows you to see and compare in one window a lot of files and folders.
- Sleep mode, restart and shutdown. Cmd-option-eject, Cmd-ctrl-eject, and Cmd-Option-ctrl-eject.
- Forced OFF. Cmd-opt-Esc - basic, but very useful.
- Quick protocol FTP. Cmd-K open a connection to the server.
MS Excel
- Edit cell. F2. Perhaps this is the main key that you need to know.
- Select the column. Ctrl-Space.
- Select series. Shift-space.
- The currency format. Ctrl + Shift + 4 (or more precisely, Ctrl + $).
- Interest format. Ctrl + Shift + 5 (or more precisely, Ctrl +%).
- By the beginning. Ctrl-Home makes the cell A1aktivnoy.
- Enter the current date. Ctrl-colon.
- Enter the current time. Ctrl-division sign.
- Copy of the cell. Ctrl - double quotes copied upper cell (without formatting).
- Format Cells. Ctrl-1 will open the format cells.
- Navigation. Ctrl-PageUp and Ctrl-PageDown.
- Multiple input. Ctrl-Enter instead of just Enter, and the data entered in one of the few selected cells will transfer the data to all other selected cells.
MS Word
- Default Formatting. Ctrl-Space in normal style for the current selection and then enter text.
- Space between paragraphs. Ctrl-0 (zero on top of the keyboard) adds or removes the interval before the current paragraph. Ctrl-1 (above the keyboard) - single line spacing of the paragraph. Ctrl-2 (above the keyboard) - a double line spacing of the paragraph. Ctrl-5 (above the keyboard) changes the line spacing to one and a half.
- Update the date and time. Alt-Shift-D - making updates to date. Alt-Shift-T - making updates of time.
7 HIDDEN FUNCTIONS OF A COMPUTER MOUSE
Keyboard and mouse are already so familiar things in our lives that it seems there certainly we can not trap any surprises. Nevertheless, it happens that all typical products are not entirely obvious properties and functions. Today we want to introduce you, and some just to recall a few hidden ways to use a computer mouse.

1. Highlight the text
We all know that it is necessary to highlight the text hold down the left mouse button and hold your cursor over the desired location of the text. However, if we need to highlight the text on the page length, that is scrollable, it is not always convenient. Therefore, use the following combination: click at the beginning of the desired location, then go to the end of the desired selection and click again, but holding the clamped Shift. All the space between the two clicks highlighted.
2. The transitions back and forth in your browser
In the browser to go to the previous or next page do not necessarily clicking on the appropriate button on the toolbar.You can simply hold down the Shift key and rotate the mouse wheel forward or backward.
3. Zoom in and out
You can zoom the display open page simply turning the scroll at the same time while holding the button on the keyboard CTRL. This method works in a large number of programs, including many image viewer.
4. Double-A and Triple-click
Everyone knows that in order to highlight the word you just need twice as fast on it to click. But if you do a triple-click, you can immediately select a paragraph of text. Try it, it is much more convenient than pulling selection cursor to the end of the paragraph.
5. Drag the right mouse button
To move files in Windows we use the drag'n'drop, that is, we take an element, drag it to the desired location and there throwing. But you can do the same thing, right click and then we will see a context menu allowing you to not only move but also copy the file and create a shortcut to the right place.
6. Selection of multiple images into text
If you are working with long text in which you need to cut only the fragments that interest you, then do not have to do it one by one. You can hold down the CTRL key and highlight the right words, sentences, paragraphs. Then copy it all in one fell swoop to the right place.
7. Open links in a new tab
Many users have long been accustomed to, that to open the link in a new tab, you can press the middle mouse button. However, if the wheel broke and do not click, it is useful to recall that the usual mouse while holding down the CTRL key leads to the same result.
IF YOUR COMPUTER IS RUNNING SLOW OR FREEZES
What should I do if my computer (laptop) running slow?
On all internet forums you can find complaints PC users about their new notebooks: the first months like everything was normal - all windows and programs open and close normally, but when only six months to go, then becomes noticeable as the speed of the laptop falls falls in dramatic fashion.
So will it cost to buy a new one again?
No way!
First, you need to change all the desktop settings. For example, if the user on the desktop are animated "wallpaper", it is not the best way will affect the overall performance of your computer, as RAM and CPU computer will only be transferred from such "wallpaper."Remove them and "hang" stationary "wallpaper".
Secondly, if you constantly install and uninstall new programs that form a set of temporary files. And this is not possible in any way to get rid of. And that temporary files tend to score HDD. In this case it is necessary to delete temporary files and to defragment the hard disk. There is another solution: buy an external HDD or a conventional HDD, which has a larger volume.
Third, we must constantly clean up and fix all registry errors in Windows.
The fact remains, but the main reason for slowing down the speed of the laptop is the registry Windows. But remove all the errors from the registry by yourself is not recommended. For this there are special registry cleaner. For Windows XP is fine traditsionnyyCSleaner.For Windows7 is better to use programs such as, Frontline Registry Cleanerili RegCure. The program is constantly updated as Windows7 so anything extra is not removed from the registry Windows7.
Fourth, install on your computer more powerful memory. With a powerful memory will work much easier and user and his computer.
Fifth, be a smart decision to uninstall any unwanted programs that do not use a computer. To do this, go to the Start menu, then Control Panel, then Add or Remove Programs. Then select the program that we do not use, click on the delete, and the program is removed. But as a rule, the "tails" of most programs remain in the registry Windows. To fully uninstall desirable at the outset to establish a program that has a useful function in the options Uninstall. If it is available, go to Start, All Programs, find the right and click on Uninstall.Everything there is nothing left. If there is no function Uninstall, it is better to use programs CSleaner, and even better Regcleaner, which are able to completely clean out all the unnecessary files from your computer.
Sixth, to change all the settings to the optimal value. For the most part, these tips will be perfect for those users whose machines are on Windows Vista or Windows 7.
Seventh, if the OS is legal, all the new settings and add-ons will be useful for
Windows. Go to Start, All Programs, and update Windows.
And last - defragmentation. Most users ignore this option. And all temporary files will still remain on the HDD even after deletion, since deleted the file headers. Defragmentation allows the files you want to combine into one. If the user does not want to defragment, then he would have nothing to remove from the HDD. In this case, with the help of useful applets Acronis broken hard drive to the desired number of bytes and the information that will not be removed in the near future, is entered in the new E or H disk. It's done. The laptop will run faster.
2. Computer freezes. What to do?
Well, let's look at three ways to help you do not restart the computer in such situations.
1 Press and hold down the Num Lock, until the system returns to its previous state. This action frees the CPU from (pardon the pun) of processes that are currently taking place.
If that does not work - go further:
2 Let us try to bring the computer out of the coma by means of antiquity Task Manager. Press simultaneously Ctrl-Alt-Delete. In the drop down box, turn off the Apps that you do not need at the moment. If this works, click OK and continue working.
3 If your computer has multiple users, again, open the Task Manager, go to the tab "Users" and select your user Nazhmaem "log out", and after re-enter the system .
And now seven tips to help avoid computer freezes.
1 At least once a week, clean history in the browser. Or even disable history saving when you turn off the computer. Well, that's if you have a computer very weak and old.
2 poudalyat temporary files stored on your computer. And do clean cookie At least once a week. 3 Remove all unnecessary programs that you no longer use.
4 Once a week, do defragment the hard disk.
5 If your computer has multiple users, make sure that there was only one user is logged in.
6 Try to periodically save your documents while you are on they are working on.
7 And do not forget to turn off the computer as expected. The Start menu. I know some people who just turn off the computer button on sistemnike. Do not do it!
On all internet forums you can find complaints PC users about their new notebooks: the first months like everything was normal - all windows and programs open and close normally, but when only six months to go, then becomes noticeable as the speed of the laptop falls falls in dramatic fashion.
So will it cost to buy a new one again?
No way!
First, you need to change all the desktop settings. For example, if the user on the desktop are animated "wallpaper", it is not the best way will affect the overall performance of your computer, as RAM and CPU computer will only be transferred from such "wallpaper."Remove them and "hang" stationary "wallpaper".
Secondly, if you constantly install and uninstall new programs that form a set of temporary files. And this is not possible in any way to get rid of. And that temporary files tend to score HDD. In this case it is necessary to delete temporary files and to defragment the hard disk. There is another solution: buy an external HDD or a conventional HDD, which has a larger volume.
Third, we must constantly clean up and fix all registry errors in Windows.
The fact remains, but the main reason for slowing down the speed of the laptop is the registry Windows. But remove all the errors from the registry by yourself is not recommended. For this there are special registry cleaner. For Windows XP is fine traditsionnyyCSleaner.For Windows7 is better to use programs such as, Frontline Registry Cleanerili RegCure. The program is constantly updated as Windows7 so anything extra is not removed from the registry Windows7.
Fourth, install on your computer more powerful memory. With a powerful memory will work much easier and user and his computer.
Fifth, be a smart decision to uninstall any unwanted programs that do not use a computer. To do this, go to the Start menu, then Control Panel, then Add or Remove Programs. Then select the program that we do not use, click on the delete, and the program is removed. But as a rule, the "tails" of most programs remain in the registry Windows. To fully uninstall desirable at the outset to establish a program that has a useful function in the options Uninstall. If it is available, go to Start, All Programs, find the right and click on Uninstall.Everything there is nothing left. If there is no function Uninstall, it is better to use programs CSleaner, and even better Regcleaner, which are able to completely clean out all the unnecessary files from your computer.
Sixth, to change all the settings to the optimal value. For the most part, these tips will be perfect for those users whose machines are on Windows Vista or Windows 7.
Seventh, if the OS is legal, all the new settings and add-ons will be useful for
Windows. Go to Start, All Programs, and update Windows.
And last - defragmentation. Most users ignore this option. And all temporary files will still remain on the HDD even after deletion, since deleted the file headers. Defragmentation allows the files you want to combine into one. If the user does not want to defragment, then he would have nothing to remove from the HDD. In this case, with the help of useful applets Acronis broken hard drive to the desired number of bytes and the information that will not be removed in the near future, is entered in the new E or H disk. It's done. The laptop will run faster.
2. Computer freezes. What to do?
Well, let's look at three ways to help you do not restart the computer in such situations.
1 Press and hold down the Num Lock, until the system returns to its previous state. This action frees the CPU from (pardon the pun) of processes that are currently taking place.
If that does not work - go further:
2 Let us try to bring the computer out of the coma by means of antiquity Task Manager. Press simultaneously Ctrl-Alt-Delete. In the drop down box, turn off the Apps that you do not need at the moment. If this works, click OK and continue working.
3 If your computer has multiple users, again, open the Task Manager, go to the tab "Users" and select your user Nazhmaem "log out", and after re-enter the system .
And now seven tips to help avoid computer freezes.
1 At least once a week, clean history in the browser. Or even disable history saving when you turn off the computer. Well, that's if you have a computer very weak and old.
2 poudalyat temporary files stored on your computer. And do clean cookie At least once a week. 3 Remove all unnecessary programs that you no longer use.
4 Once a week, do defragment the hard disk.
5 If your computer has multiple users, make sure that there was only one user is logged in.
6 Try to periodically save your documents while you are on they are working on.
7 And do not forget to turn off the computer as expected. The Start menu. I know some people who just turn off the computer button on sistemnike. Do not do it!
WONDER PHOTO EDITOR
I've tried many photo editors. A recently discovered a new one. He met me before, but for some reason did not lead it never work. And here recently downloaded and decided to try it. He impressed me with its simplicity, ease of operations and stunning end result! This Photoinstrument. The program of work with pleasure! After processing the photos in it for many years younger! I recommend to all!
The conversion of black and white photography in color
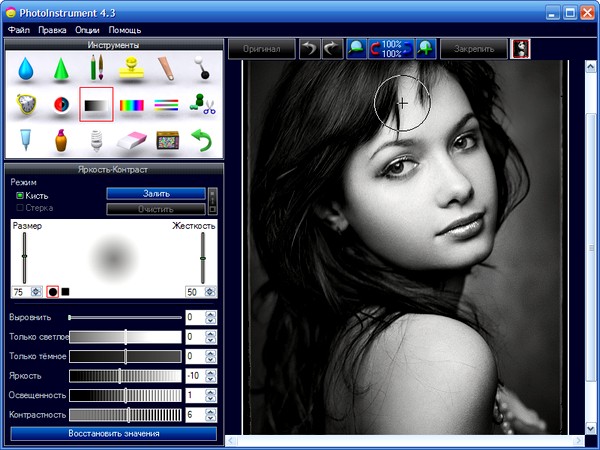

Glamour photo processing
PRIOR TO ..
And after ..

The program has a built-in tutorial video
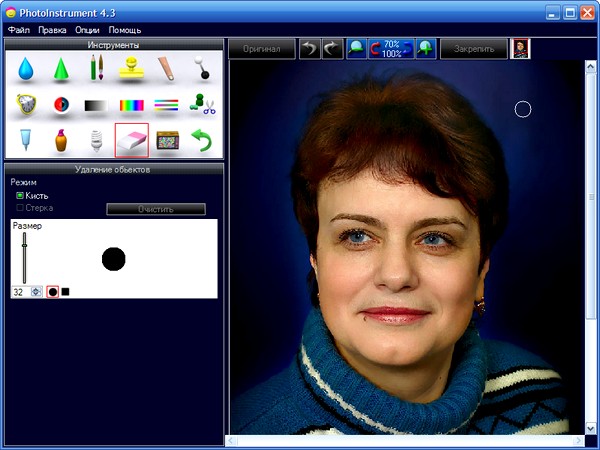
The program has a function of removing unwanted objects from a photo.
If anyone is interested, you can download: file size 4.6 mb
The installer program operates in a quiet setting. After you run the installation program does not appear any windows reflecting the installation progress. The program defaults to drive C: / Programm Files . After 2-3 minutes looking for it there. The "cured" and no codes and serial numbers are not required. Enjoy your work!
Subscribe to:
Posts (Atom)
Labels
COMPUTER
(38)
LAPTOP
(36)
INTERNET
(32)
Games
(21)
NOTEBOOKs
(18)
Data Recovery
(16)
MOUSE♥
(12)
WINDOW XP
(12)
Domains
(11)
WebSite
(9)
WeB
(8)
DESKTOP
(7)
HARD DISK
(7)
Microsoft
(7)
PC SECURITY
(7)
SOFTWARE♥
(7)
WINDOWs
(7)
Audio Video Streaming
(6)
KEYBOARD
(6)
ONLINE
(6)
CDs
(5)
GOOGLE♥
(5)
Streaming
(5)
CD
(4)
Computer Certification
(4)
MS OFFICE
(4)
Web Design
(4)
FOLDERS
(3)
HACKS♥
(3)
USB
(3)
VIRTUAL MEMORY
(3)
VIRUS
(3)
GPS
(2)
HIDDEN APPS
(2)
Programmer
(2)
SEO
(2)
VISTA
(2)
Articles
(1)
Computer Forensics
(1)
Consumer Electronics
(1)
DOWNLOAD
(1)
EDUCATION
(1)
FDISK
(1)
FILES
(1)
Microprocessor
(1)
NETWORKING
(1)
NUM LOCK
(1)
Outlook 2007
(1)
PhotoShop
(1)
RAPIDSHARE
(1)
REGISTRY
(1)